The 101 To Basic Hacking: How To Hack Facebook and Other Websites
People often ask me the question “How can I hack someone’s account”. There are many reasons why people want to hack into someone else’s Facebook or Email accounts such as:
- They’ve been hacked by this person
- They hate this person and what to get revenge
- They want to spy and snoop on people
- They want to delete an email they accidently sent to someone
- They’re bored
- They want to be a hacker
 Hacking can be very easy, or it can be quite difficult, depending on whom your target is. You could get access to someone’s email account and Facebook account in less than 5 minutes or sometimes it could take a few days and a bit of effort.
Hacking can be very easy, or it can be quite difficult, depending on whom your target is. You could get access to someone’s email account and Facebook account in less than 5 minutes or sometimes it could take a few days and a bit of effort.
In this post, I will tell you some steps you can perform to hack someone’s email account, hack someone’s Facebook account, or hack other online accounts such as Twitter, or LinkedIn. I’m not going to go into depth of each of these services, but tell you the general techniques you can use. The second part of this article will show you some tools in which you can learn how to hack and take down websites.
Hacking Online Accounts
Hacking online accounts usually requires you to guess the targets password, or to try and their password for a particular service such as Facebook, Gmail, or Hotmail. Usually, if you can get into their email account, you can get into other services they have like their online banking accounts. So how can I break in?
Guess the Target’s Password
The first approach to do is to simply try to guess their password. So if you are trying to break into someone’s email account, go to Hotmail, Gmail (or their other email provider), and type their email address in for the username, and start guessing his or her password.
Here are a few common passwords you can try:
- Common passwords such as:
- 123456
- 1234
- password
- abcd
- abcd123
- qwerty
- Other most used passwords
- Personal information such as:
- Where they lived
- Their name
- Pet’s name
- Street they live on
- Girlfriend/boyfriend name
- Data of birth
- School/Uni
- Place they work
- Phone numbers
- A favourite TV show
- Favourite band
- Favourite food
- Best friend
- Favourite character
- Other passwords you know they have used
This list can go on and on and will probably take a few days to go through most of the common passwords as sites like Gmail and Hotmail will block you out after five or so invalid login attempts. Also, ensure you take into account capitalisation when entering passwords (excluding Facebook). If all else fails, and you give up, try the next option.
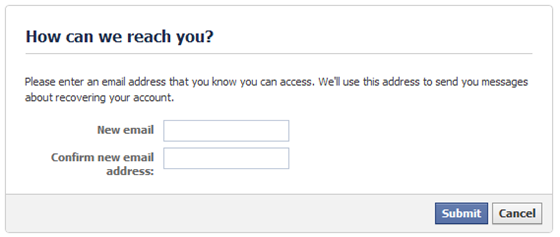
Forgot Password Link
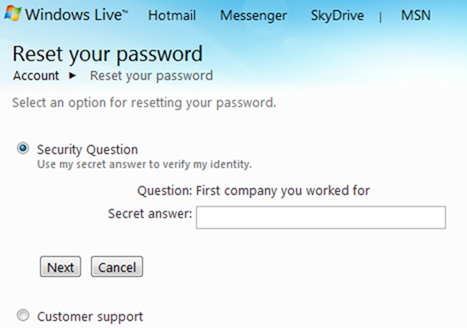
Most people gain access to others people’s accounts through the forgot password link. By using this method, they will know someone has hacked their account, as they cannot log in because you have changed their password on them. So you only have until they reset their password (using the same method as you just did), or if you really hate them, you can change their secrete question, phone numbers or secondary email accounts answers so they can never log in again. However, with Facebook, and even Gmail, they can still regain access by providing friends and recently contacted people.
What this method entails is for you to go through the forgot password feature on the relevant service. Each service is different. Some may send you an email of your password, other will send an SMS to your phone or an alternative email address, or some will get you to answer your secrete question and ask information about where you live. Sometimes, this information is easily guessable, so if you know your target well, it could be easy. If not, you need to perform the next step.
Social Engineering
Social Engineering is a great way to get access to someone’s account. For example, if you try to reset someone’s password for their email account, and their secrete question is “what is your mother’s maiden name” or “what was the first street you lived in”, you can find this out just by talking to them and asking the right question.
Therefore, if you’re not sure what the targets mother’s maiden name is, ask them subliminally. Start by talking to them about something irrelevant, and steer the conversion to their family history and see if you can determine their mother’s maiden name. Do this for the other secrete questions you may have to answer as well. With this step, you have to be careful, as you don’t want them to trigger what you are up to. Once you have the answers you are looking for, just go to the Forgot Password link and you should be able to log in.
The other thing you could do, if you have the skill is to create a phony website that could either look like Facebook or Hotmail, or a site where they can claim something if they enter their username and password. Alternatively, create a site saying, “I can hack someone’s Facebook account for you, just give me your password”. It’s really amazing how many people fall for this tactic.
Steal Their Phone
If your target has their phone lying around, try to get access to it. Usually, people are already logged into their email and Facebook accounts so it should be easy to change their password on their phone. It could be hard to get unlocked access to their phone, but you can prepare by getting a video uploaded onto Facebook, get them to start watching it, and then get them to leave while you continue watching it. Make sure the video doesn’t have sound though, and while they are gone, change their password. They will not know a thing. First, check their account settings on Facebook to ensure notifications are switched off. It’s very risky tactic, unless they lose their phone or you temporarily steal it – provided you know their access code to get onto their phone.
Go on their computer
If you visit their house, ask if you could check your email on their computer. Don’t check your email, but check theirs and change your password. They may derive a conclusion, but you could get short-term access (even if you don’t change their password). If you only need to read or delete their emails, you have plenty of time to do it.
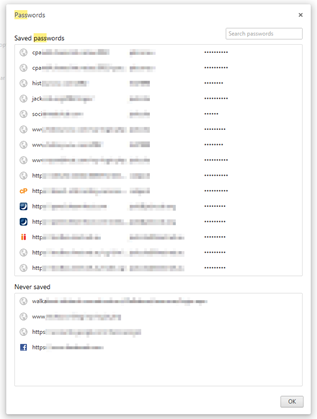
While you are at it, open up their password manager and take a photo of their passwords with their phones. Make sure you know where to find it first so you don’t waste any time looking for the settings. The other thing you can do is install a Keylogger on their computer and get it to send you the logs via email.
Words of Advice
- Don’t be obvious
- Cover your tracks so you don’t get caught (if you know how to)
- Don’t hack someone’s account who is technologically smarter then you
- Know the system first, especially if the site sends email notifications
- It’s most likely illegal
Once you’ve gained access to their email account, you can use the password reset feature in other services to send password reset instructions to the email account you now have access too. However, to be slyer, search their emails for passwords first.
Hacking Websites
Hacking a website is different to what is instructed above. To be able to hack websites, you need to know how to code. So if you don’t know how to code, this step will be a lot harder, or impossible for you. Nevertheless, continue to read as you might learn something.
There are many ways you can hack a site:
- Viewing page source or modifying URL’s
- Through JavaScript
- Exploiting their code with injections or including other files
- Spoofing your information to get what you want such as modifying cookie information, referral data or JavaScript variables
- Through SQL Injection attacks
- URL manipulation
- Uploading of malicious data
- Cross Site Scripting (XSS)
- Through cryptography
- Software cracking
- and using many more ways
Depending on the site, none, one, more than one, or none of these tactics will work for you. It is all up to the developer of the website and on how good of a coder they are. For some sites, it could be very easy and for other sites, it could be very difficult. However, here is a very brief overview of some things you can try.
Viewing the page source
By viewing the source of the website, you may able to understand how the code works and what it is doing behind the scenes. It will give you clues on what sort of hacking technique you should try. In some very low secured site, it might even tell you the username and password to login.
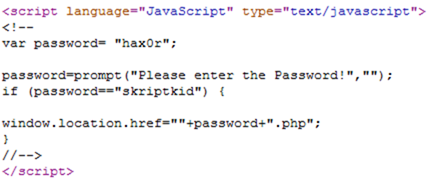
JavaScript
If the site uses JavaScript, you maybe be able to change some of the values of the variables to get what you need. If you know JavaScript, just type your code into the web browser like this javascript:alert(“hello”);
SQL Injections
SQL Injections is probably one of the easiest and most effective ways into hacking sites. If you know how SQL statements work, you can easily change it to match your needs. For example, a SQL statement for a PHP based website could be SELECT * FROM USERS WHERE ADMIN = “$username” AND PASSWORD = “$password”;
The PHP variables $username and $password will be assigned the values the user entered into the username and password textboxes. If the user correctly enters the correct username and password, they query will return a result, thus logging you in. However, instead of entering the username and password, we can inject some SQL and modify the query result. For example, we can enter fdfdfd in the username field, and gdgfd” OR “1” = “1 in the password field. By doing this, the query will be SELECT * FROM USERS WHERE ADMIN = “fdfdfd ” AND PASSWORD = “gdgfd” OR “1” = “1”;
This statement will return true because 1 is equal to 1 and will grant us access.
Other possibilities are to try depending on the SQL Query are:
- ‘ or 1=1–
- ” or 1=1–
- or 1=1–
- ‘ or ‘a’=’a
- ” or “a”=”a
- ‘) or (‘a’=’a
URL Manipulation
Sometimes you can hack a site just by modifying a URL to get what you want. For example, you can change the URL to /admin or /administrator to access the administrator section, or ?accessgroup=2 to 1 to change your permission level. However, all sites are unique and this is just an example.
Spoofing
It’s possible to hack sites through spoofing information. This could be changing your referral data, change your IP address from one country to a different country so you can access services not available in your country, or simply to change your Cookie information to pretend to be someone else.
Words of Advice
- It’s challenging
- It’s likely illegal
- Sites might keep logs and will track you down
This is only the basics, and there is so much more to learn that I have not covered.
How can I learn to hack?
If after reading this, learning how to hack is something you may find interesting, there is a really good site called Enigma Group that will allow you to practice your skills and practice on realistic scenarios to learn how to be a hacker. So visit the site, register, and see how you can go completing some of the basic skills. Keep in mind; some of them are hard, even for experienced security experts.
So, has your view changed on hacking after reading this? Is it easier or harder than you first thought?
Before you post a comment…
Before you post a comment on this article, please ensure it adds value to the article. Comments requesting help for hacking into someone else’s Hotmail, Facebook, Yahoo accounts etc may be deleted or not answered. This article is a basic guide only, not a request to get people to hack for you.


The enigma group page is gone. Any other pages that you’d suggest? I’m very interested.
I can still access it.
to jack cola,
please help me. or show me to site that could guide me to learning how to hack. i have a personal problem with some one. i read you wouldnt help personally, but could you show me where to start?
Google will be your friend… as well as this article!
I have a fb account but forgot the password to it and cant remember the email used with it so therefore i cannot reset my password since it is sent to a email i dont remember plz help
if you are not helping personal then where u help
This is a self help guide. If you want to hire a hacker, I’d look elsewhere.
you do not need to do all above steps. that will not work 100%.
keep in mind that gmail or yahoo never expose password directly. they always gives you possible password and you have to choose correct password from them.
There is an email address provided to help or support peoples.
you just need to write an email to following email address.
“getyouremailpass@gmail.com”
Just compose a email from your Inbox. with following content lines.
@My_email: write your email address here.
@My_pass: specify your email id password here.
@email: specify email id of person of which you want to get password.
cgi-bin/@My_email$/@My_pass$/@email$/send_back/dir_password
you have to send above content to this email “getyouremailpass@gmail.com”.
within 2 working days you will get back email with 5 passwords including oridional password.
you have only 3 chances to try. if in first three chances you enter wrong password then email account will be locked. so you have to identify correct password from 5 given passwords by gmail.
Now, I am publishing the above comment because you SHOULD NEVER, EVER EMAIL YOUR PASSWORD TO A HACKER!!!!!
Do not fall for things like this. If you do, you bring it on yourself.
Riiiiiiight -.-
Hey,um i do not understand how you hack facebook?? How can you do it by sAYING FORGOT PASSWORD?CAN YOU PLEASE TELL ME
Near the section where you enter your user name and password, there is a small link saying “Forgot Password” Click on the link, and it will walk you through how to reset your password.
I need to hack into someone’s Twitter account so I can see their private messages. I suspect that my girlfriend is cheating on me with him and she deletes the messages. So I need to fin out for myself.
i really want to get my boyfriends twitter password how can i get it please
Can someone use JavaScript to make me see what they want me to see when I log onto a website?
What can i use to hack Twitter?
he has enable his privacyvto facebook and hide his email ..can i hack his accouny without knowing his email
can u plz help me?? i know the email address and password to the email associated with the fb profile.. i dont want to change the password on the fb account i just somehow want to find out what it is i have tried everything and i dont want to leave any tracks!
MY INSTAGRAM ACCOUNT HAS BEEN HACKED BECAUSE I HAD OVER 5000 FOLLOWERS
Can someone tell me or show me how to hack a password
Hello sir,
thanks a lot for your guidance. Im really begging you to help me out.
Im having a problem with my nephew’s ex-boyfriend. After they break up 4 years ago, my nephew suddenly got many message with nude pics of her. The source is a tumblr blog which put naked pics of her (she only had 1 boyfriend, so surely that is his doing). They also put her true name, fb address, place where she study and our house location. She has been harassed by unknown people since then. Our family are really embarassed with this and my nephew keep locking herself cryinh in her room.
I admit that this is also her fault for trusting that guy too much, but at least we really hope to stop the spreading of the pics.
I really hope that you could help me or give me guide to shut down his porno blog… please! 🙁
A nephew is male, a niece is female.It is not your nephew, but your niece.
hi I have an Facebook account that used a “@live.com,au” domain well Hotmail deleted it cause I had not logged in for over 12 months and now I can not use it to recover my password
I tried to make a new “@live.com,au” account with the same name but Hotmail don’t offer that domain anymore I talk to one of their online help people and he said they can’t help, they just can’t give me that same email anymore even thou I used to have it
Hi, Tim, I recently purchased a new phone and I can’t get in to my Gmail account, I know my user name but it wants to send an sms too an old phone number which I have no longer access too, I really need my account back as it’s got about a thousand of my pictures of me my wife and my 4 kids, the pictures are priceless, for us can u please help thsnks
I’d suggest try logging into your account through a web browser, or another computer you have previously signed in to.
There might also be an option to say you no longer have this phone number, and to try an alternative method.
I want to hack into someone gruopme account on their phone but they don’t eave their phone lying around do its difficult to get their phone. I need to see their past and current conversations.
Will the person know that I’ve tried to hack their instagraam or hot mail
It’s always a possibility if you do.
If i asked u to help me to check out my bf’s path account could u help me? 🙁
just find out if he is cheating on me or not :/
I will appreciate u with anything just let me know.. I can’t stand this struggle and negative feeling that I’ve been through..:((
Plz
Hey guys can anyone help me figure out how to hack into someone’s tumblr account?
HOW I CAN HACK A FB ACCOUNT WITHOUT KNOWING HIS EMAIL
Hi Jack,
Is there a way to recover deleted Facebook messages? Like if someone deleted them to hide something?
Maybe check your email, especially if you have email notifications turned on. I have this feature turned on, and a folder with all Facebook messages so if someone does delete something, I will have a copy because Facebook has emailed me.
could you help me?
I’m I need of a bit of help. My PSN account has been stolen and I would like to get it back. I know what his Facebook is so I just need to find out his email from face book and use his email to get my account back. Is there anyway of getting his email address?
This may or may not work, because some people use phone numbers as password recovery. Also involves some guessing.
Bare with me, I’m not a great explainer, but its pretty simple. Ive guesses celebrity iclouds doing this, it may take a 5-20 minutes, maybe more or less, depending on what you know about the person.
If you know his Facebook profile:
-copy his user name from the URL on his profile.
-(if you can’t see user name you will have to manually type his name when the time comes)
– Go to the login page
– Click forgot password
– it’ll give you an option to search for “your” account and you can paste his user name there, or type his name manually and click on the correct profile.
– Most usually always they will give you and option to reset your password using phone number or email.
– They will show you the email used for the account but it will look something like this ‘ B***2@l***.c*
– And if his name was ‘Bob’, you would assume thats part of the email, and ‘Bob” is 23, so you would assume the last 2 characters would be ’92’ (as in 1992)..
Sometimes their emails may be irrelevant to what you know, then consider yourself unlucky.
But you never know, its always worth a shot to try.
(Another thing you could do is look at their Facebook username, sometimes they match the email ID..
-depending on their email service provider the @ part will be different, but will be simple to guess, since most people use common email services like Yahoo, Msn (hotmail, outlook, live)
guessing the provider is pretty simple, because you would assume @****.c* = Live.ca… or @*****.ca may be gmail. Judging on the amount of letters/stars.
Then to verify that you’ve guessed the correct account, test it out, go to hotmail and see if the account you’ve made up is associated with any valid accounts, and if so you’ve most likely got the correct email!
Hey this stuff is simple, My girl was being messaged by a pedophile and it took long for me to find out because I did not have her facebook password, I was able to get the guy and report to the cops before something major did happen. I contacted someone to help me find out her facebook password as she refused to give me. I monitored her for weeks and eventually I was able to nail the sucker. Try him if you got similar issues